A recent article was posted yesterday by malware researchers at Fortinet, discussing a new malware that exploits the Windows kernel module. This malware utilizes a position-independent shellcode called Donut to load .NET Assemblies, PE files, and other Windows payloads. The attackers can leverage this technique to gain higher privileges, evading security mechanisms and executing arbitrary code.
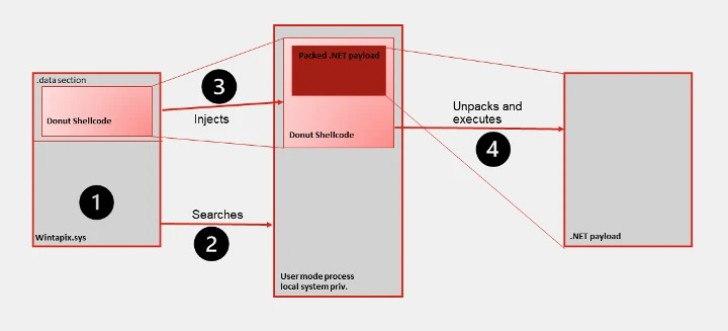
Fortinet’s malware analysts recently discovered and analyzed a new malware called WINTAPIX. Within the WinTapix.sys driver, they identified a position-independent shellcode called Donut, which enables the execution of executables from memory with specified parameters. Despite the fact that the malicious driver was compiled back in March 2020, it was only reported to VirusTotal in February of this year.
The primary purpose of this malware is to elevate system privileges. By executing within the kernel, an attacker can effectively bypass or disable various local security mechanisms, enabling privilege escalation and arbitrary code execution. Consequently, this malware serves as the initial stage of a multi-staged attack on a host or network.
What enhances the potency of this malware is its ability to establish persistence within the Windows Registry, allowing it to operate even in safe mode. Moreover, the driver provides a stable backdoor and proxy functionality, enabling the execution of arbitrary code, file uploads and downloads, as well as serving as a pivoting point to other hosts.
Despite the alarming nature and relative ease of deploying this malware, its initial loading onto a system is impeded by an invalid signature. Consequently, an effective countermeasure to mitigate this risk is Driver Signature Enforcement, which ensures that only Microsoft-signed drivers can be loaded and installed on the system.
